CMMC Gap Assessment: IMPORTANT Things to Know
Quick guide to CMMC gap assessment process
INTRODUCTION
A CMMC gap assessment, also called a gap analysis, is when an organization identifies all current CMMC processes and practices then compares them to the processes and practices needed to optimize performance or meet CMMC compliance requirements. Generally, a gap analysis allows an organization to identify areas of improvement.
But let’s start from the beginning:
In January 2020, the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) in conjunction with the Department of Defense (DoD) stakeholders, University Affiliated Research Centers (UARCs), and Federally Funded Research and Development Centers (FFRDC) released the first version of the Cybersecurity Maturity Model Certification (CMMC) framework was released.
CMMC’s primary goal is to establish a standardized cybersecurity approach across all companies in the defense industrial base (DIB) supply chain, including suppliers who subcontract through larger defense equipment manufacturers. Depending on where your organization sits in the DIB supply chain, your compliance requirements may differ from larger prime contractors.
As companies DoD contractors build out their CMMC compliance programs, they need to understand the requirements and compliance gaps existing in their current controls landscape.
QUESTIONS This article will answer the following questions:
Conduct a Free Gap Assessment Now!
Begin the process of increasing your competitive advantage by maturing your security posture with our Free Assessment Tool
Start A FREE GAP ASSESSMENTWhat is CMMC?
As a maturity model, not regulation, CMMC sets out best practices that companies can use to establish policies and procedures, enabling them to create benchmarks for measuring their cybersecurity program effectiveness.
As a maturity model, CMMC allows companies to start with the controls they have in place and build more robust programs by adding more controls and processes. Smaller contractors with less mature programs can begin with basic cyber hygiene requirements, then build their programs up by using the controls outlined in CMMC.
At its core, CMMC looks to create cyber resiliency across the DIB supply chain. All DoD contractors will need to review their information security programs, locate compliance gaps, and engage in remediation activities by 2025.
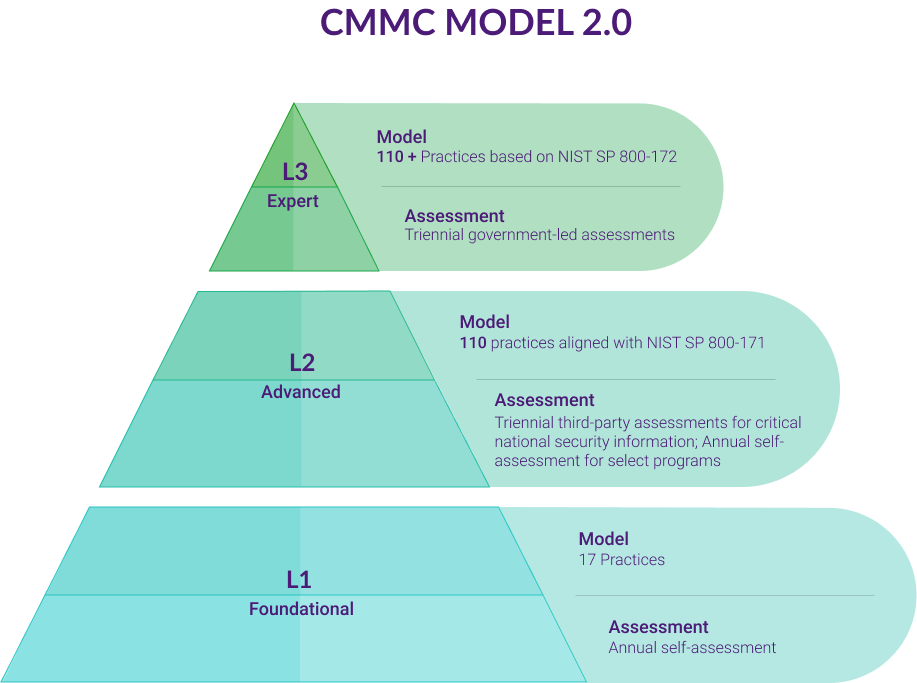
How to determine your CMMC Level?
Determining your CMMC level requires you to think about two things. First, you need to consider the type of information you manage. Second, you need to determine the processes and practices you currently have in place.
Conduct a Free Gap Assessment Now!
Begin the process of increasing your competitive advantage by maturing your security posture with our Free Assessment Tool
Start A FREE GAP ASSESSMENTWhat data qualifies as FCI?
The National Archives Controlled Unclassified Information blog defines FCI as
information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, but not including information provided by the Government to the public (such as on public websites) or simple transactional information, such as necessary to process payments.
Companies maintaining FCI must follow the “Basic Safeguarding of Covered Contractor Information Systems” requirements outlined in Federal Acquisition Regulation (FAR) 52.204-21. The FAR continues to define “information” as “any communication or representation of knowledge such as facts, data, or opinions, in any medium or form, including textual, numerical, graphic, cartographic, narrative, or audiovisual.”
FCI is the broadest information category, and being compliant with FAR 52.204-21 closely aligns with CMMC Level 1. As organizations build out their readiness assessments, FCI, and FAR 52.204-21 should be the first compliance gap that companies review
Information that is collected, created, or received pursuant to a government contract
FCI
Information that is not marked as public or for public release.
Minimum Cybersecurity Requirements in a non-federal information system: Basic Safeguarding Clause: 48 CFR 52.204-21*
CUI
Information that is marked or identified as requiring protection under the CUI program.
Minimum Security requirements in a non-federal information system: NIST SP 800-171
PUBLIC INFORMATION
Public information or information marked for public release.
Minimum Security requirements in a non-federal information system: None
*also excludes simple transactional information
What data qualifies as CUI?
The Defense Counterintelligence and Security Agency (DCSA) defines CUI as “government created or owned information that requires safeguarding or dissemination controls consistent with applicable laws, regulation, and government-wide policies.”
The CUI Registry, managed by the National Archives, lists all approved CUI categories and subcategories. The registry’s twenty Organization Index Groupings break down into 125 CUI categories. Among the CUI categories are:
- Controlled Technical Information
- DoD Critical Infrastructure Security Information
- Patent Applications
- Contract Use
- Inventions
- Homeland Security Agreement information
The CUI registry then defines each category independently. For example, “Controlled Technical Information” is “technical information with military or space application that is subject to controls on the access, use, reproduction, modification, performance, display, release, disclosure, or dissemination.” The definition offers the following examples of technical information:
- research and engineering data,
- engineering drawings,
- specifications,
- standards,
- process sheets,
- manuals,
- technical reports,
- technical orders,
- catalog-item identifications,
- data sets,
- studies and analyses and related information,
- computer software executable code and source code.
Because CUI encompasses a wide array of information, determining what data a company maintains and where it stores the information can be difficult. Additionally, since managing CUI triggers the need to be Level 3 compliant at some point, any organizations maintaining this category of information need to engage in gap analysis to determine whether their current cyber resiliency practices and processes align with CMMC Levels 2 or 3.
What controls are necessary to meet CMMC compliance?
As a maturity model, CMMC provides controls enabling organizations to start where they are and then extend additional security controls across their ecosystems. Before engaging in a readiness assessment, companies need to start by looking at the information they maintain, their current security controls, and determine whether a compliance gap exists.
Most companies should manage to meet the Level 1 requirements with little effort. However, CMMC rapidly escalates the number of required controls as organizations transition toward Level 3 compliance. Part of the reason that CMMC takes a cybersecurity maturity approach is to enable organizations within the DIB supply chain to focus their cyber resiliency strategies on the information they maintain as part of their business model.
Level 1 CMMC compliance
At Level 1, organizations need to show that they have basic practices, even if they lack documentation. Basic cybersecurity hygiene aligns mostly with FAR 52204-21.
- Limit access to authorized users and processes acting on behalf of users and devices
- Limit access to types of transactions and functions necessary to complete job function
- Verify and control/limit connection to and from external systems
- Control information posted or processed on publicly accessible systems
- Identify users and processes acting on behalf of users and devices
- Authenticate identities before granting access
- Sanitize or destroy media containing FCI
- Limit physical access
- Escort visitors and monitor their activity
- Maintain physical access audit logs
- Control and manage physical access devices
- Monitor, control, and protect data at information systems’ external boundaries and key internal boundaries
- Implement subnetworks for publicly accessible system components
- Identify, report, and correct information and information system flaws in a timely manner
- Protect against malicious code at appropriate locations within systems
- Update malicious code protections
- Perform periodic system scans and real-time file scans

All organizations need to engage in these seventeen basic security practices. Most likely, smaller organizations have already implemented these controls, but they may be done on an ad hoc basis rather than formalized into a documented program. However, while Level 1 maturity should be easy to meet, the lack of repeatable and documented processes may compromise the organization’s cyber resiliency.
Level 2 CMMC compliance
Since Level 2 certification acts as a “transition” between the informal Level 1 and full compliance with NIST 800-171, it requires companies to create formal practices and processes.
To be Level 2 compliant, organizations need to add 48 of the 110 controls contained in NIST 800-171. Some of these controls include:
- Employing the principle of least privilege
- Monitoring and controlling remote access sessions
- Create and retain system audit logs and records to enable monitoring, analysis, investigation, and reporting of unlawful or unauthorized system activity
- Review audit logs
- Establish security training and awareness programs
- Establish and maintain baseline configuration and system inventories
- Establish and enforce minimum password complexity policies
- Establish an operational incident-handling capability
- Require multifactor authentication to establish nonlocal maintenance sessions via external connections and terminate them when maintenance is completed
- Limit access to CUI on system media to authorized users
- Establish personnel security practices
- Perform and test data back-ups
- Establish a risk management function
- Scan for system and application vulnerabilities
- Remediate vulnerabilities
- Establish, update, and periodically assess system security plans
- Use encrypted sessions for the management of network devices
- Monitor system security alerts and advisories and take action in response
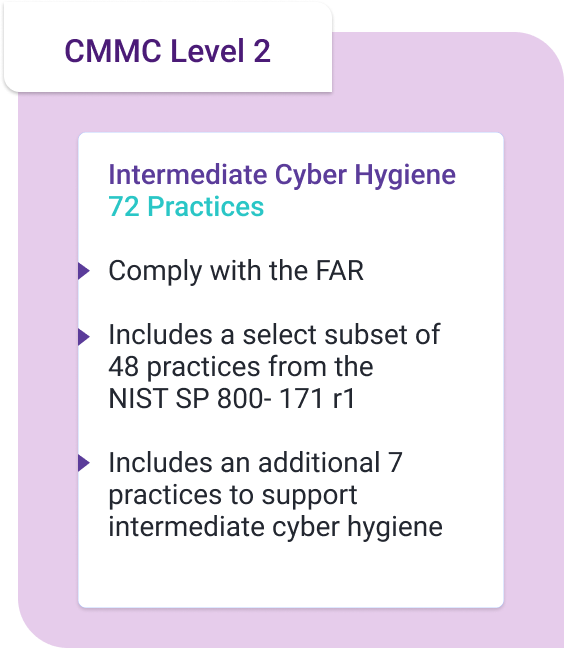
Although this list represents a small smattering of required controls, organizations engaging in a gap assessment may find themselves struggling because Level 2 requires more sophistication and documentation. Level 2 steers organizations towards greater cyber resiliency by focusing on audit documentation and establishing continuous monitoring over controls’ effectiveness.
Level 3 CMMC compliance
Level 3 certification means that an organization has established and implemented all 110 controls required by NIST 800-171. Organizations with Level 2 certification need to incorporate an additional 45 controls to meet Level 3 compliance.
Examples of these controls include:
- Establishing separation of duties controls
- Protecting wireless access using authentication and encryption
- Encrypting CUI on mobile devices and mobile computing platforms
- Defining CUI data handling procedures
- Collecting audit information into one or more central repositories
- Correlate audit record review, analysis, and reporting process for investigation and response
- Provide security awareness training around insider threats
- Define, document, approve, and enforce physical and logical access restrictions
- Apply a deny-by-exception policy to prevent unauthorized software use or deny-all, permit-by-exception policy for accepted software use
- Use multi-factor authentication for local privileged accounts as well as for network access for privileged and non-privileged accounts
- Disable identifiers after a defined inactivity period
- Track, document, and report incidents to internal and external designated officials/authorities
- Mark media with necessary CUI markings and distribution limitations
- Control access to media containing CUI and maintain accountability during transport
- Regularly perform complete, comprehensive, and resilient data back-ups
- Periodically perform risk assessments to identify and prioritized risks
- Develop and implement risk mitigation plans
- Establish ongoing controls monitoring to ensure continued effectiveness
- Employ FIPS-validated cryptography
- Implement cryptographic to protect CUI during transmission unless otherwise protected by physical safeguards
Protect the confidentiality of CUI at rest - Employ spam protection mechanisms

Organizations that obtain Level 3 certification have a set of controls enabling cyber resiliency and engage in continuous monitoring. These programs, while not the highest level of CMMC sophistication, require a greater level of formalization, monitoring, documentation, and governance than many companies may have previously established.
What is a gap assessment?
A gap assessment, also called a gap analysis, is when an organization identifies all current processes and practices then compares them to the processes and practices needed to optimize performance or meet compliance requirements. Generally, a gap analysis allows an organization to identify areas of improvement.
Because CMMC is a maturity model intended to help the DIB supply stream enhance cybersecurity, it relies primarily on looking for ways to improve security controls continuously.
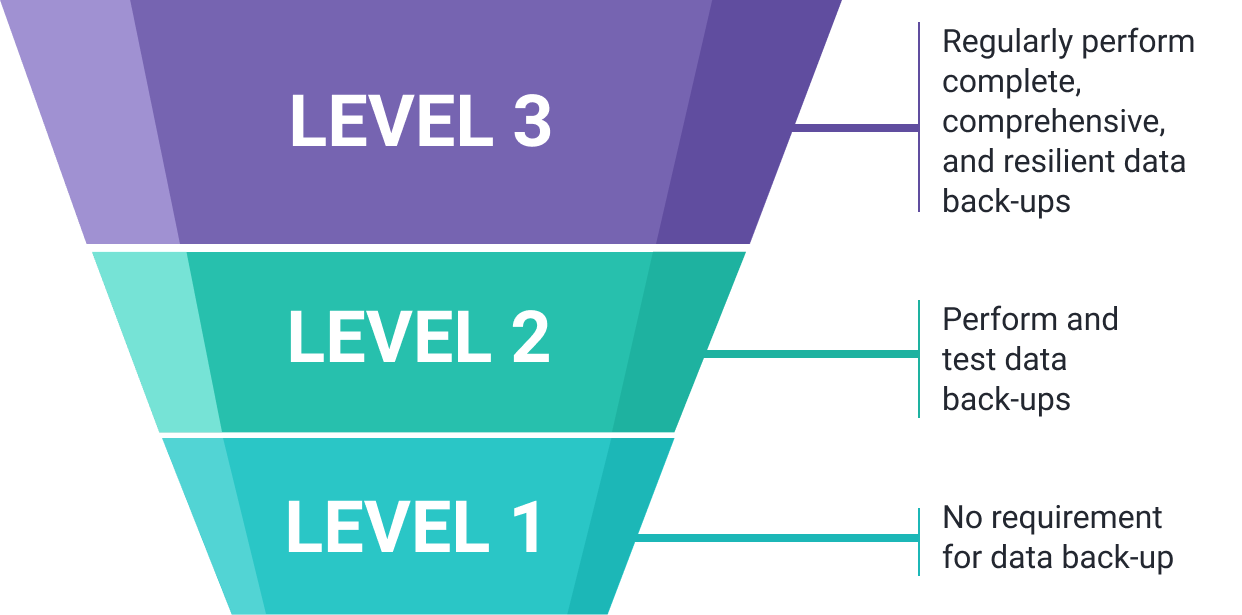
For example, a look at the data back-up processes listed for CMMC Levels 1 through 3 provides insight into what a gap analysis does
Organizations certified to Level 1 that do not have back-up practices would have a “compliance gap” as they move toward Level 2 certification because they have not met the compliance requirement of having appropriate data back-up. However, as part of their cybersecurity maturity process, they close the gap with practice remediation of this weakness. Meanwhile, a Level 2 certified organization must have a data back-up practice, but to get certified for Level 3, they need to add regular data back-up practices. Again, the organization must engage in a remediation process to remove the compliance gap.
The difference between the controls set and the controls needed are a compliance gap that the organization must address.
How is a gap assessment different from a risk assessment?
A risk assessment is when an organization identifies assets, reviews risk, analyzes the impact risks can have, and then decides to accept, transfer, refuse, or mitigate the risk. In other words, risk assessments enable flexibility for how a company chooses to protect data.
A gap assessment lacks the flexibility inherent in a risk assessment. With a gap assessment, an organization looks at the controls they have in place and compare those to what the regulation or standard says they need to have.
Since CMMC establishes certain prescriptive controls, organizations need to start with a gap assessment. However, since NIST 800-171 requires a risk assessment, organizations seeking Level 3 CMMC certification will need to engage in a gap analysis and a risk assessment.
How to perform a CMMC gap assessment?
Performing a CMMC gap analysis is about choosing the certification level that aligns with long term business goals.
Determine current state
The first step in the CMMC gap analysis process is looking at the current business needs. An organization that only requires CMMC Level 1 certification today may have less work to complete than an organization that needs to meet CMMC Level 3 requirements.
Once the organization understands the type of information it currently handles, it needs to look at the current state of its controls. Then, the company needs to compare the existing controls to the CMMC Level control requirements. This activity is the first stage of the gap analysis, identifying the current control landscape to the controls necessary to maintain current contracts.
Any controls that the organization needs to establish or enhance to meet its current business needs should be prioritized.
Review business goals
Next, the organization needs to determine whether it has long-term business goals that require additional CMMC certification. For example, a new company may have small contracts and maintain only FCI. However, as the business scales, it will likely need to maintain CUI as well.
Because CMMC focuses on cybersecurity maturity, it also makes it easier for businesses to mature their business in parallel with their security program. Now, the organization needs to iterate its security control landscape by looking at the additional controls it needs to align with its business goals.
Iterate the gap analysis process
Now that the organization knows the CMMC Level certification it needs to achieve its business goals, it needs to identify the necessary additional controls.
The process is the same as the initial gap assessment. The organization looks at the controls in place for current business needs, then compares those to the controls necessary to meet future business goals. After comparing the two, the organization establishes a timeline for completing the next CMMC Level certification requirements, prioritizing activities based on criticality to the business goals and security needs.
Conduct a Free Gap Assessment Now!
Begin the process of increasing your competitive advantage by maturing your security posture with our Free Assessment Tool
Start A FREE GAP ASSESSMENTWhat are the challenges companies face when doing a CMMC gap assessment?
For organizations looking to become CMMC certified, a gap assessment becomes more challenging as they move through the process.
For example, organizations moving from Level 2 to Level 3 need to measure their Level 2 control landscape to Level 3’s additional 45 controls. However, when looking at the data back-up control, the difference between performing and testing back-ups and regularly engaging in data back-up might seem to overlap.
Moreover, as the organization moves from 15 controls to 110 controls, continuously cross-checking across the levels can become time-consuming and disorganized.
Who is the CMMC-AB?
The DoD incorporated the CMMC Accreditation Body (CMMC-AB), authorizing it as the sole authoritative source for operationalizing assessments and training. The CMMC-AB establishes the CMMC certification process and acts as the primary arbiter of all cybersecurity maturity compliance activities.
The CMMC-AB manages the CMMC ecosystem, including:
- CMMC Third-Party Assessor Organization (C3PAO) applications
- Designing the provisional program
- Training C3PAO
- Establishing criteria for becoming a C3PAO
- Publishing the criteria
- Working with licensed partner publishers
- Licensing training providers
All organizations that seek to be CMMC certified, regardless of level, need to engage in a gap assessment, hire a C3PAO, and submit the assessor’s report to the CMMC-AB.
Conduct a Free Gap Assessment Now!
Begin the process of increasing your competitive advantage by maturing your security posture with our Free Assessment Tool
Start A FREE GAP ASSESSMENTWhat is the CMMC Marketplace?
The CMMC-AB established the CMMC Marketplace to provide:
- Access to a searchable database for current partner organizations Certified Third-Party Assessment Organizations (C3PAOs), Registered Provider Organizations (RPOs), Licensed Partner Publishers (LPPs), and Licensed Training Providers (LTPs)
- Access to searchable database for certified and registered individuals such as Certified Assessors (CAs), Certified Professionals (CPs), and Registered Practitioners (RPs)
- All stakeholders accounts that enable them to upload information and update profiles instantly
- Additional information like relationships between individuals and their affiliated companies
In short, the marketplace acts as one-stop shopping for organizations looking to get certified so that they can find the necessary compliance services. For companies doing program pre-assessments or looking to complete a gap analysis, the CMMC-AB Marketplace can help locate professionals with the required credentials.
Certified Assessor (CA)
A CA has completed the CMMC-AB training to engage in an official CMMC assessment. CAs can be certified for Level 1, Levels 1 through 3, or Levels 4 and 5. CAs manage program assessments that are later forwarded to the CMMC-AB.
CAs move from one level to the next based on the number of assessments they have completed. For example, a CA-1 Assessor needs to complete three Level 1 assessments to be certified as a CA-3 Assessor. To move to a CA-5 Assessor, the person needs to complete fifteen assessments.
CA-5 Assessors are credentialed across all maturity levels and authorized to supervise Certified Professionals across any maturity level.
Certified Professional (CP)
Certified Professionals are authorized to participate as part of an assessment team overseen by a CA. Unlike CAs, CPs cannot complete an official security assessment. However, a company can use a CP’s compliance services to engage in pre-assessments and establish best practices.
Although eligible to become CAs, they can also work as an employee within an organization to help their company understand the requirements of CMMC.
Registered Provider Organization (RPO)
RPOs employ staff with CMMC training and are bound by the CMMC Code of Conduct. RPOs can deliver non-certified CMMC Consulting Services, including targeted CMMC audit coordination and assessment preparation. They cannot, however, engage in official assessments. RPOs are an excellent source of compliance services for managing a gap analysis or pre-assessment.
Registered Practitioners (RP)
RPs are individuals who have completed the basic CMMC training program that allows them to include targeted CMMC methodology and Code of Conduct. RP certifications are valid for one year and enable people to register on the CMMC-AB Marketplace. These individuals can help a company’s cybersecurity maturity gap analysis by suggesting best practices and helping set controls. Their CMMC training gives them the information necessary to determine where organizations have a compliance or security gap and enable remediation of these weaknesses.
Licensed Training Providers (LTP)
LTPs develop, maintain, deliver, and train people to become CPs and CAs. They can be colleges, universities, online schools, professional schools, internal corporate training departments, and other consumer learning providers. The use approved curriculums and facilitate courses run by CMMC-AB Certified Instructors.
To be licensed, LTPs must have at least two years’ experience in providing training with proven capacity to provide online and/or in-person educational services and have at least three client references.
All LTPs must deliver at least one Certified Class per year that uses CMMC-AB Approved Training Material (CATM) and use CMMC-AB Certified Instructors.
Licensed Partner Publishers (LPP)
LPPs provides educational materials and courses that LTPs can use teaching CMMC standards, practices, implementation, scenarios, and best practices. The LPPs generate CMMC-AB approved curriculum for online or in-person courses developed based on CMMC learning objectives.
To be licensed, LPPs need to publish at least 200 hours of coursework/curriculum in technology, cybersecurity, auditing, or similar content, have at least two years’ history publishing this content, and provide at least three client references.
All content maps to CMMC-AB certification exams, maps 100% of exam objectives, and must be approved by the CMMC-AB.
What is the Interim Rule?
Released on September 29, 2020, the Defense Federal Acquisition Regulation Supplement (DFARS) “Assessing Contractor Implementation of Cybersecurity Requirements” (Interim Rule) will be effective on November 30, 2020. The Interim Rule requires that all companies looking to bid on DoD contracts implement a National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 Scoring Methodology assessment and CMMC assessment.
Notably, the Interim Rule states that contractors are responsible for “information flow down to its subcontractors in a multi-tier supply chain.” This requirement means that companies are responsible for ensuring that their subcontractors meet and maintain the appropriate CMMC certification.
The Interim Rule requires that companies looking for DoD contracts do self-assessments outside of CMMC certification requirements. These program assessments, however, align with NIST 800-171, ultimately helping organizations that need Level 3 certification.
What are the differences between CMMC and the Interim Rule?
The CMMC and Interim Rule differ in several ways. While they overlap with one another, they also have unique uses and requirements.
Levels
CMMC sets levels based on the type of information an organization collects, processes, and stores. Level 1 requires organizations maintaining Federal Contract Information (FCI) to establish basic cyber hygiene practices. Levels 2 through 5 set out additional controls and monitoring requirements for companies that maintain FCI and Controlled Unclassified Information (CUI). As a cybersecurity maturity model, CMMC creates smaller steps that organizations can take as they establish controls, engage in gap assessments, and add more controls to enhance their security monitoring.
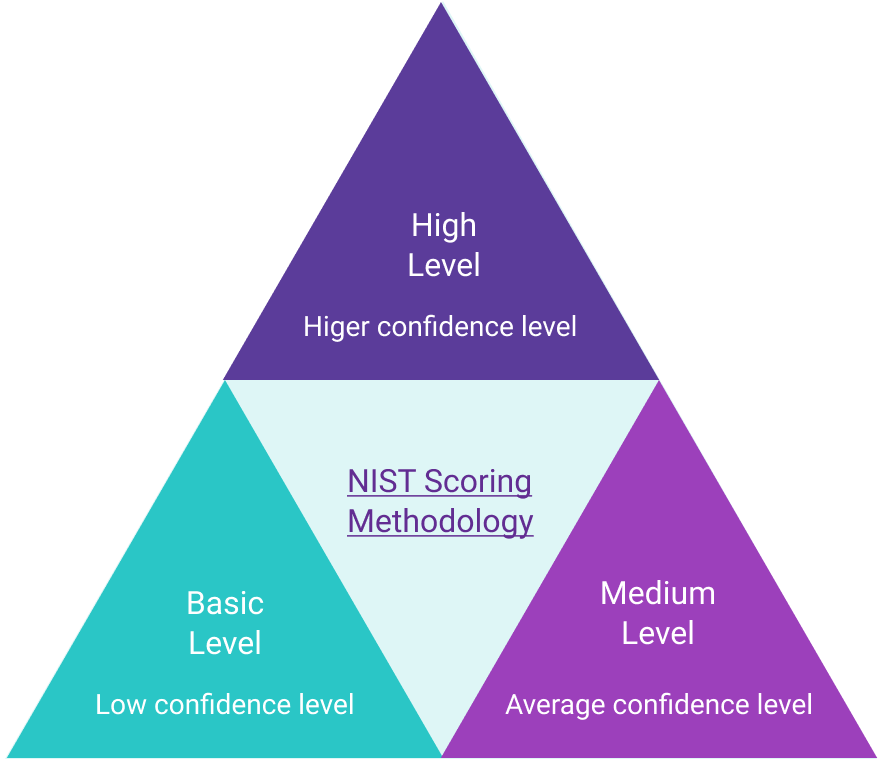
On the other hand, the Interim Rule uses the NIST Scoring Methodology that has three levels – basic, medium, and high – reflecting the depth of the assessment and the confidence that the DoD can have over the assessment results. For example, a Basic Assessment is a contractor’s self-assessment without any DoD oversight, leading to a low confidence level. Meanwhile, a High Assessment is conducted by trained DoD professionals either on-site or virtually, leading to higher confidence because the assessment is completed independently. Additionally, the NIST Scoring Methodology requires a risk assessment, not a gap analysis, giving companies more flexibility around how they set certain controls.
Assessment Type
CMMC is a certification that requires the company to hire a CMMC Third-Party Assessor Organization (C3PAO). The NIST Scoring Methodology is either a self-assessment or conducted by DoD personnel.
Controls
The Interim Rule focuses only on controls listed in NIST 800-171. CMMC requires those controls and builds in additional practices and processes, including those from NIST SP 800-171B, DFARS Clause 252.204-7012, and 48 CFR 52.204-21. A company that needs to meet Level 1 certification needs to prove compliance with 17 practices, while a Level 5 certification requires 171 practices.
What is the NIST 800-171 Scoring Methodology?
The NIST 800-171 Scoring Methodology takes a different approach to compliance than CMMC does. With CMMC, organizations gradually add controls until they meet the necessary requirements.
The NIST 800-171 starts by assigning an organization a total of 110 points, then subtracts points for unimplemented controls. Although the NIST Scoring Methodology does not prioritize controls, it does use a weight-based system that indicates controls considered more impactful. For example, the Scoring Methodology values user access as 5 points, meaning that without this control other derived controls are less effective.
How does the NIST 800-171 Self-Assessment help engage in a CMMC gap analysis?
Ultimately, any organization that needs to be certified to CMMC Level 3 or above will need to implement all NIST 800-171 controls. Ultimately, companies can use the NIST Scoring Methodology as part of their readiness assessment and gap analysis.
The Scoring Methodology helps organizations determine their current readiness level by listing control types and weighting the most important controls. NIST notes that the Scoring Methodology intends to demonstrate appropriate control implementation, giving organizations that need to enhance their cybersecurity maturity suggestions. The methodology does not place a value judgment on how companies meet the compliance, but it provides a way for companies to evaluate their current security program for compliance gaps.
Once a company completes the NIST 800-171 self-assessment process, it needs to document the score in the Supplier Performance Risk System (SPRS). The information that the company needs to input includes:
- Assessment date
- How many points out of 110 the company scored
- Scope of the Basic Assessment
- Date that a score of 110 will be achieved
Because the self-assessment requires companies to set a date by which they believe they will have remediated all compliance gaps, the self-assessment’s weighted scoring can help organizations prioritize their next steps.
Ultimately, by completing the NIST Self-Assessment, organizations will have better insight into their current cybersecurity maturity and can better plan their CMMC certification strategy.













